Employee monitoring software, also known as user activity monitoring (UAM) software is used to monitor employee computer activity to identify and stop insider threats, for employee training, to review employee performance, and to monitor productivity. The ultimate goal of employee monitoring software is to increase productivity and reduce or eliminate insider threats.
An employee monitoring software tracks all user activity for apps, websites, emails, network etc. while at work. In addition to basic employee monitoring, Teramind’s PC monitoring software also includes insider threat detection, third-party vendor monitoring, data loss prevention, risk management, legal and compliance features as part of their monitoring suite.
Teramind pack workforce productivity optimization, time tracking, project management, employee productivity monitoring, and other additional value-added features too. This has helped boost the popularity and usefulness of computer monitoring software from its original surveillance and tracking purpose to the territory of business intelligence (BI), HR management, finance and other enterprise productivity tools.
That’s why it’s not surprising to see nearly 80% businesses use some form of user computer monitoring software. Teramind’s employee monitoring software has powerful productivity features for day to day decision making, performance reviews, and workplace safety.
Teramind’s PC monitoring software also provides protection from legal liability, and as a defense from sabotage and IP theft.
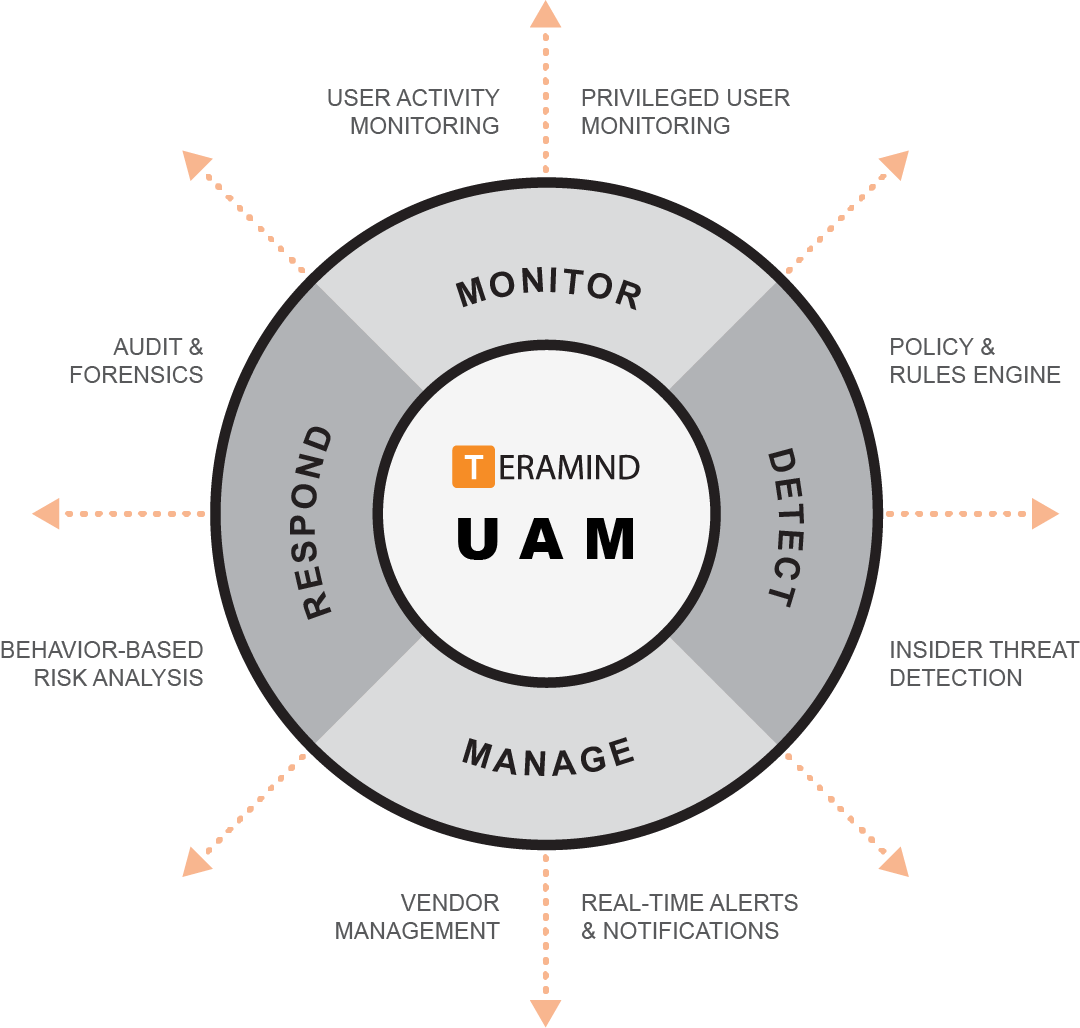
Features
Teramind’ employee computer monitoring software monitors all employee activity covering 12+ system objects like: web/apps, social media, emails, keystrokes, network etc. Even on-screen content with OCR is monitored with employee monitoring software. Create monitoring profiles for employees, groups or departments based on your monitoring needs.
Intelligent behavior analysis can detect malicious activity and anomalies that indicate deviation from normal behavioral baseline. Dynamic risk scoring and vulnerability scanning identifies insider activity before they represent a real threat.
Teramind’s PC monitoring software immediately notifies you about harmful employee activity and insider threats. Automatically block any harmful action, lock out the user or take remote control of their computer before any data theft, sabotage or fraudulent attempts.
Teramind’s computer monitoring software comes with hundreds of pre-built rule templates, activity classification lists and data categories to let you get started the right way. Create your own policies and rules with an intuitive, visual rule editor. Use natural English, regular expressions and sample conditions to easily define your requirements.
Use computer monitoring software to define which apps, websites, and social media you consider productive. Teramind provides in-depth reports on how your employees utilize each app and website. Identify employee performance with active vs. idle time analysis. Establish a continuous feedback loop to refine and adjust your organizational workflow through tracking of schedules, projects and employee engagement rate for overall productivity boost.
Video recording of all employee work, audio recording, session recording, immutable logs, alerts and optional OCR search are just a few examples of Teramind’s computer monitoring software powerful audit and forensic capabilities. Together they provide a vast collection of investigative data to locate the source of an insider threat with pinpoint accuracy.
Teramind’s employee monitoring software features cover third party vendors and remote users who have access to your critical systems. This computer monitoring software enables you to control vendor management and third-party SLA and decreases the chances of cyber threats.
Teramind’s employee computer monitoring software can be used to create activity and schedule based rules to support several common compliance requirements. These requirements include: implementing audit trails (GDPR), limiting unauthorized login (ISO 27001), prevent unencrypted file transfers (PCI DSS), reporting, and more.
Benefits:
- Increase Productivity
- Reduce Administrative Work
- Increase Employee Engagement
- Identify Process Gaps
- Detect Insider Threats

